Your Info
04 May, 2008
Apa itu PROXY SERVER
Proxy server adalah sebuah komputer server atau program komputer yang dapat bertindak sebagai komputer lainnya untuk melakukan request terhadap content dari Internet atau intranet.
Proxy server bertindak sebagai gateway terhadap dunia Internet untuk setiap komputer klien. Proxy server tidak terlihat oleh komputer klien: seorang pengguna yang berinteraksi dengan Internet melalui sebuah proxy server tidak akan mengetahui bahwa sebuah proxy server sedang menangani request yang dilakukannya. Web server yang menerima request dari proxy server akan menginterpretasikan request-request tersebut seolah-olah request itu datang secara langsung dari komputer klien, bukan dari proxy server.
Proxy server juga dapat digunakan untuk menyelamatkan jaringan pribadi yang dihubungkan ke sebuah jaringan global (seperti halnya Internet). Proxy server memiliki lebih banyak fungsi daripada router yang memiliki fitur packet filtering karena memang proxy server beroperasi pada level yang lebih tinggi dan memiliki kontrol yang lebih menyeluruh terhadap akses jaringan. Proxy server yang berfungsi sebagai sebuah "agen keselamatan" untuk sebuah jaringan pribadi, umumnya dikenal sebagai firewall.
29 April, 2008
Peripheral
A computer peripheral is any external device that provides input and output for the computer. For example, a keyboard and mouse are input peripherals, while a monitor and printer are output peripherals. Computer peripherals, or peripheral devices, are sometimes called "I/O devices" because they provide input and output for the computer.
Some peripherals, such as external hard drives, provide both input and output for the computer.
15 April, 2008
Storage Devices
Hard DriveThe hard drive is the primary device that a computer uses to store information. The hard drive stores programs, data files, saves files, and organizes files. The hard drive is located inside the computer case. The hard drive, magnetically stores data on stacks of rotating disks called platters.
Floppy Drive
The floppy drive stores and retrieves information on a floppy disk.
CD -ROM DriveCD-ROM is a device that reads information stored on a compact disc. CD-ROM stands for Compact Disc Read Only Memory. One CD is equal to the space in over 40 floppy disc.
Removable Hard DiskA zip disk is a removable disk that holds a large amount of information. A zip disk can be used to achieve, protect and transfer large amounts of data.
Information size measurements
- Kilobyte (KB)
- One kilobyte equals about 1024 bytes
- 1KB is about 140 words, about a half page of typed double-spaced text (words only)
- Megabyte (MB)
- One megabyte equals about 1000 KB
- One megabyte equals about 1,000,000 bytes
- One megabyte equals about 500 pages of text, or one large book
- Gigabyte (GB)
- One gigabyte equals about 1000 MB
- One gigabyte equals about 1,000,000 KB
- One gigabyte equals about 1,000,000,000 bytes
- One gigabyte equals over 1,000 books of text
Categories of Computers
 Personal computers
Personal computers
Personal computers are desktop computers designed for an individual's use. They run programs designed to help individuals accomplish their work more productively. Servers
Servers
Servers are not designed to be used directly. They make programs and data available for people hooked up to a computer network, a collection of computers connected together so that they can exchange data.
Minicomputers
Minicomputers are multi-user systems that can handle the computing needs of a smaller corporation or organization. Many people use them simultaneously by means of remote terminals or personal computers.
Mainframes
Mainframes are huge, multi-user systems designed to handle gigantic processing jobs in large corporations or government agencies.
Supercomputers
Supercomputers are ultra fast computers designed to process hugh amounts of scientific data then display the underlying patterns that have been discovered.
What is the Internet?

The Internet is millions of computers throughout the world, all connected by cables. In professional networking diagrams, the Internet is always displayed as a image besides. The cloud is a good analogy because just as a cloud is made up of millions of tiny water droplets, the Internet is made up of millions of computers.
You connect to the Internet through a device called a modem, and an ISP (Internet Service Provider). Your ISP might be TMnet, Jaring, Celcom Broadband, Maxis, or any of several hundred other companies.
The Keyboard

The keyboard is a means of interacting with your computer. You really only need to use the keyboard when you're typing text. Most of the keys on the keyboard are laid out like the keys on a typewriter. But there are some special keys like Esc (Escape), Ctrl (Control), and Alt (Alternate). There are also some keys across the top of the keyboard labeled F1, F2, F3, and so forth. Those are called the function keys, and the exact role they play depends on which program you happen to be using at the moment.
Most keyboards also have a numeric keypad with the keys laid out like the keys on a typical adding machine. If you're accustomed to using an adding machine, you might want to use the numeric keypad, rather than the numbers across the top of the keyboard, to type numbers. It doesn't really matter which keys you use. The numeric keypad is just there as a convenience to people who are accustomed to adding machines.
The Mouse

Your mouse probably has at least two buttons on it. The button on the left is called the primary mouse button, the button on the right is called the secondary mouse button or just the right mouse button. I'll just refer to them as the left and right mouse buttons. Many mice have a small wheel between the two mouse buttons. ow you use the mouse are as follows:
*
Point: To point to an item means to move the mouse pointer so that it's touching the item.
*
Click: Point to the item, then tap (press and release) the left mouse button.
*
Double-click: Point to the item, and tap the left mouse button twice in rapid succession - click-click as fast as you can.
*
Right-click: Point to the item, then tap the mouse button on the right.
*
Drag: Point to an item, then hold down the left mouse button as you move the mouse. To drop the item, release the left mouse button.
*
Right-drag: Point to an item, then hold down the right mouse button as you move the mouse. To drop the item, release the right mouse button.
cont.....
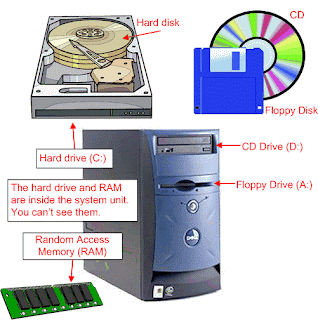
The floppy drive and CD drive are often referred to as drives with removable media or removable drives for short, because you can remove whatever disk is currently in the drive, and replace it with another. Your computer's hard disk can store as much information as tens of thousands of floppy disks, so don't worry about running out of space on your hard disk any time soon. As a rule, you want to store everything you create or download on your hard disk. Use the floppy disks and CDs to send copies of files through the mail, or to make backup copies of important items.
What is Hardware?
Not everybody has exactly the same hardware. But those of you who have a desktop system, like the example shown in Figure 1, probably have most of the components shown in that same figure. Those of you with notebook computers probably have most of the same components. Only in your case the components are all integrated into a single book-sized portable unit.
13 April, 2008
Random Access Memory (RAM)
- Store data and instructions that are used by the CPU to perform some task.
- These instructions are usually loaded into RAM from a secondary storage device.
- RAM is also used to store instructions that tell the CPU how to work with its parts. These instructions are usually called drivers.
- The instructions in RAM are constantly changing, depending on the needs of the CPU.
- The instructions in RAM are volatile.
- When the computer is turned off the information in RAM disappears.
- The information in RAM needs to be saved to secondary storage before the computer is turned off.
- Access to information is random access.
Read Only Memory (ROM)
- Stores instructions that are used by the CPU
- Tells the CPU how to be the kind of computer it is, for example a Windows, Macintosh, or Play Station computers.
- Tells the CPU how to work with the different parts of the computer
- ROM can also hold programs that are directly accessed by the CPU. One such program is the self-test when the computer is first turned on. The self-test tests to seem if all the parts on the main circuit board (mother board) are working correctly.
- The instructions in ROM can not usually be changed
- The instructions are built into the electronic circuits of the chips
- These instructions in ROM are called firmware
- To change the instructions in ROM you need to usually change the chips or do some other special process that is normally not available to an average user.
- The instructions in ROM are nonvolatile. They stay in ROM even when the computer is turned off.
- Access to information is random access.
- Random access means that any piece of information in ROM can be accessed at any given time without access other information first. It is a lot like the tracks on a music CD. You can access any track at any time and in any order.
- The other kind of access is sequential access. You must access the information in the order that they are located. This is a lot like a music tape. You must play the songs in order, or you have to fast forward past songs to get to the one you want.
Central Processing Unit (CPU)
Does all of the work for the computer
- Does all of the mathematics, mainly addition
- Does all the logical comparisons of values
- Directs the flow of data in a computer
- Controls the operation of the parts of the computer
Today, all CPUs are microprocessors
- A microprocessor is a complete computer on a silicon chip
- A microprocessor does all of the functions of a computer
- stores data and instructions waiting to be used
- follows changeable instructions
- does input, processing, and output
CPUs have three basic parts
- The Arithmetic Logic Unit (ALU)
- does all of the mathematics in a computer
- does all of the logic comparisons of values
- some common logic comparison symbols
- = equal to
- < less than
- > greater than
- <= less than or equal to
- >= greater than or equal to
- <> not equal
- The Control Unit
- directs the flow of information into the CPU and/or memory or storage
- controls which instructions the CPU will do next
- Registers
- Used to store data and instructions inside the processor
- Size of the registers can affect the speed and performance of the processor
Speed of CPUs
- The speed of CPUs is measured in hertzs.
- A hertz is on cycle per second.
- Need to measure time to determine cycles per second
- All computers have a clock built into them for timing the cycles
- The clock is usually located in a small metal box on the motherboard.
- Today, many CPUs can complete over six (6) instructions per second.
- Speeds of modern CPUs
- Most computers have a CPU that can do more than 400 MHz.
- MHz stands for megahertzs
- A MHz is 1,000,000 cycles per second.
- Computers will soon be at speeds of over a gigahertz, 1,000,000,000 Hertzs.
Inside view of system unit
Motherboard - The motherboard is the main circuit board of a microcomputer. It is also known as the mainboard or system board.
CPU - The CPU is the central electronic chip that determines the processing power of the computer.
Memory - Memory is the part of the computer that temporarily stores applications, documents, and stem operating information.
Bus - A bus is an electronic line that allows 1s and 0s to move from one place to another.
Expansion Slots - Expansions slots appear on the motherboard. They are sockets into which adapters are connected.
Ports and Connectors - A port is a connector located on the motherboard or on a separate adapter.
Bays - A bay is a space inside the computer case where a hard drive, floppy drive or CD-ROM drive sits
Power Supply - A power supply changes normal household electricity into electricity that a computer can use.
Sound Components - A sound card lets a computer play and record high quality sound.
06 April, 2008
Pengenalan
Pada tahun 1996 program KDP telah diperluas ke 90 buah sekolah dan pada 1999 ke 110 buah sekolah menengah melalui surat siaran KP(PPK) 8601/01/0400/Jld.Xll (91) bertarikh 11 Februari 2000. Pada tahun 2002, satu surat perkeliling KP(BS-PP)8786/004/35 (8) bertarikh 20 Mac 2002 telah memaklumkan kepada semua sekolah yang dibekalkan makmal komputer di bawah Program Pengkomputeran Sekolah Kementerian Pelajaran Malaysia supaya melaksanakan program Literasi Komputer di tingkatan 1 dan 2.
Pada tahun 2005, selari dengan perkembangan teknologi maklumat dan komunikasi serta dapatan kajian keperluan yang dijalankan di bawah program Partners In Learning (PIL) antara Kementerian Pelajaran Malaysia dengan Microsoft (Malaysia) Sdn. Bhd., kandungan program Literasi Komputer sekolah menengah telah disemak semula. Hasil dari semakan semula ini, program ICT Literacy for Secondary School diperkenalkan dan akan dilaksanakan di sekolah menengah mulai 2007. ICT Literacy for Secondary School Guideline disediakan sebagai panduan bagi membantu guru untuk melaksanakan program Information and Communication Technology Literacy for Secondary School dengan jayanya.
Dengan adanya program ini, usaha Kementerian Pelajaran Malaysia untuk melengkapkan pelajar dengan kemahiran asas teknologi maklumat dan komunikasi dapat direalisasikan. Program ini merupakan langkah permulaan ke arah menyediakan tenaga kerja teknologi maklumat dan komunikasi pada masa akan datang. Disamping itu, program ini dapat membantu kerajaan dalam usaha mengurangkan jurang digital di kalangan pelajar luar bandar dan bandar.
Akhir kata, usaha menyempurnakan garis panduan ini telah melibatkan banyak pihak iaitu pensyarah universiti, Institut Pendidikan Guru, guru dan pegawai Kementerian Pelajaran. Sehubungan itu, Pusat Perkembanagan Kurikulum merakamkan setinggi-tinggi penghargaan dan terima kasih di atas sumbangan kepakaran, masa dan tenaga yang telah diberikan bagi menghasilkan garis panduan ini.
(MAHZAN BIN BAKAR SMP, AMP)
Pengarah
Pusat Perkembangan Kurikulum
Kementerian Pelajaran Malaysia
OBJECTIVES
At the end of this programme, pupils should be able to:
• acquire and apply ICT knowledge and skills creatively to assist them in their aily life;
• share ideas and information among themselves, within and beyond the school
environment; and
• demonstrate responsibility and accountability towards ICT infrastructure and its used.
INTRODUCTION
The Computer in Education (CIE) programme was launched and piloted in 60 secondary schools in 1992 for all form one and form two pupils. Each computer lab in these schools was equipped with 20 desktop computers and a server. A guideline for teachers was also prepared to help teachers implement this programme through the circular KP (PPK) 8601/01/0400/Jld II (91) dated 17 February 1992 (Appendix A).
This programme was well received and found to be beneficial to pupils in enhancing learning in the area of ICT. Consequently, the programme was extended to 90 more schools in 1996, and 110 other schools were given the same opportunity in 1999 through a letter, KP(PPK) 8601/01/0400/Jld. XII (91) ated 11 February 2000 (Appendix B). In 2002, the service circular KP(BS-PP)8786/004/35 (8) dated 20 March 2002 (Appendix C) stated that all schools equipped with computer labs implement Computer Literacy Programme in form 1 and 2.
Due to the rapid development of ICT, the need eventually arose for a review of the Computer Literacy Programme. In 2005, through a need analysis carried out under the Partners In Learning (PIL) Programme, the contents of the Computer Literacy Programme for secondary schools were reviewed. It was found that there was a need to cater for various levels of capability in ICT skills among pupils. This necessarily demands formulation of a programme that introduces pupils to various entry points of ICT knowledge. It was also discovered that there was a need to expose pupils to other domains of ICT such as Programming, Networks and the Internet.
As a result of the need analysis conducted, Information and Communication Technology Literacy (ICTL) for Secondary School Programme is introduced and will be implemented in year 2007 to form 1 and form 2 pupils in all secondary schools equipped with computer labs.
In drawing up this guideline, due consideration has been given to the content of ICTL for Primary Schools Programme. This is to ensure the continuity of ICTL for Primary Schools Programme. The ICTL for Secondary Schools Programme takes up from this foundational grounding and seeks to provide pupils with greater access to information, to expand their knowledge and skills; and also to enable them to fully utilise technology in various fields. At the same time, moral values are emphasized in the implementation of this programme.
This ICTL for Secondary School Guideline is designed to provide teachers with an idea of the scope of the contents and relevant teaching and learning strategies. Coupled with this guideline, the content specification is provided to facilitate the implementation of this Programme. Teachers are encouraged to use other resources or create their own modules based on the content scope provided and the pupils' computer skills ability.
04 April, 2008
COMPUTER LAB RULES AND REGULATIONS
Below are suggestion of rules and regulations for computer lab users.
1. Pupils are prohibited to enter the lab unless authorised by the teacher.
2. Scan diskettes before using them.
3. Report all problems related to the system to the teacher.
4. Do not attempt to repair or tamper with lab equipment.
5. Be responsible when using equipment, software and facilities in the lab.
6. Do not move any equipment from its original position.
7. Do not remove or load any software into the computer.
8. Do not change the settings in the computer.
9. Save all work in external storage device and not in the computer.
10. Do not bring in bags, food and drink into the lab.
11. Turn off the computer accordingly after use.
12. Switch off all power supplies before leaving the lab.
13. Internet facility is strictly for educational purposes only.
14. Teachers should record the use of computer lab in the lab log book.
15. All users should record the use of computers in the computer log book.
16. The Lab should be kept clean and tidy at all times.






























